Analysis Of Malware.Unknown.exe - Introduction To Basic Static Analysis.
A step by step guide on how to perform basic static analysis on malware artifacts plus tools to work effectively.
Moving from the unknown to knowing what a piece of binary is doing, we perform some basic static analysis. This is the process of analyzing the binary without detonating (executing) it.
Performing some basic static analysis on the species, we collect the hashes of this file.
A hash value is a unique value that corresponds to the content of the file. Rather than identifying the contents of a file by its file name, extension, or other designation, a hash assigns a unique value to the contents of a file.
To do this, run the following commands
sha256sum.exe Malware.Unknown.exe.malz
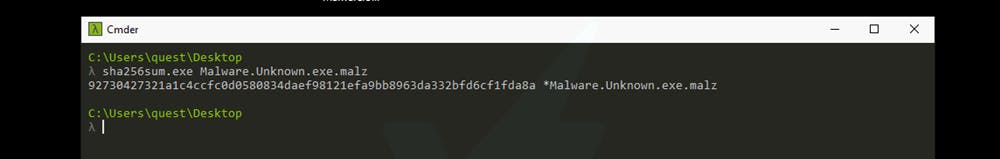
Submitting the hash 92730427321a1c4ccfc0d0580834daef98121efa9bb8963da332bfd6cf1fda8a to a database like virustotal, we learn that the file is malicious.
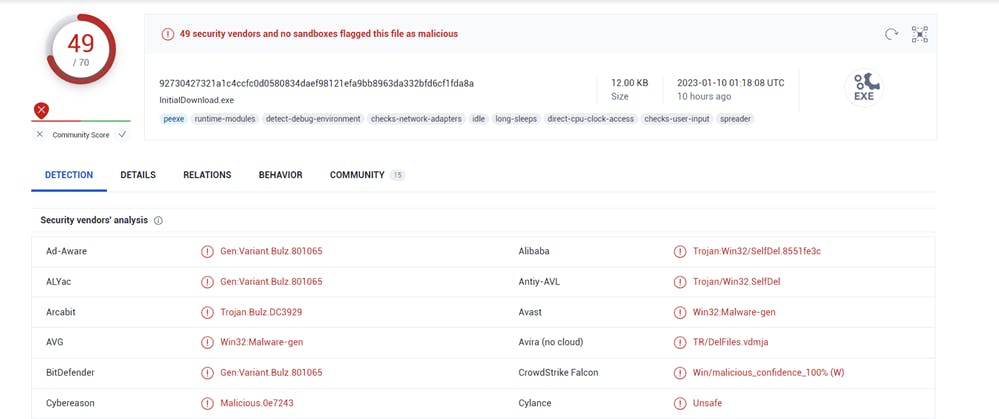
If we take a look at the "details" tab we find a lot of information here including basic properties, history, names, etc. Mind you, the information is here because a handful of people have uploaded this sample in the past.
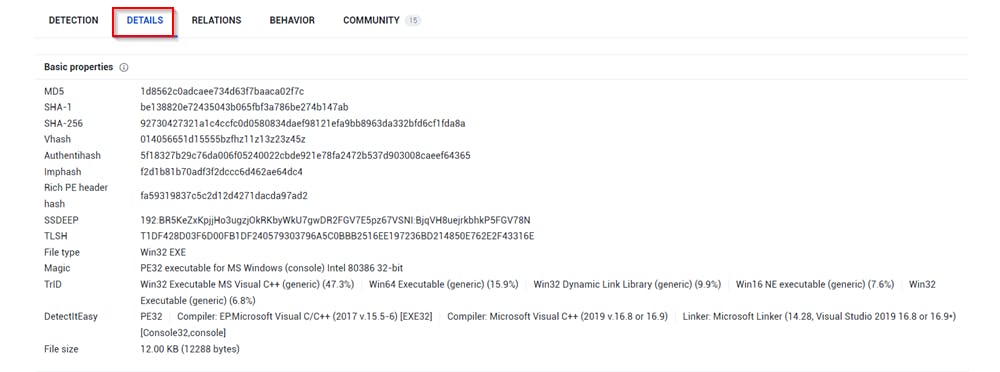
That cannot be said for any new malware species should we find one in the wild. Anyways, let's get back to the lab, shall we?
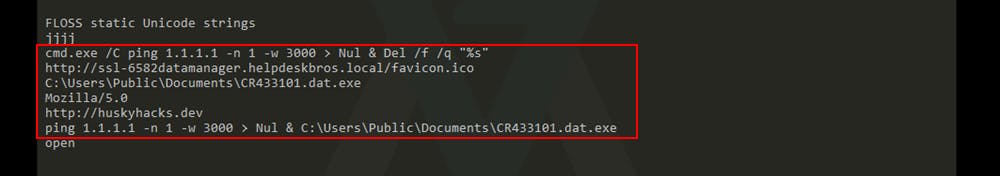
Running floss on the sample we get a lot of output but some strings look very interesting. A string is an array of characters and at some point, a threat researcher needs to have this in their code that tells a sample where to go or what to do.
As mentioned by Matt in his course, he did not do much to modify the binary which gives us access to the path of malware from the original compilation

At the end of the pile, we find some interesting strings that we would dig deeper into to find out what they're doing in the dynamic analysis phase.
Opening up the binary in peview we get more data.
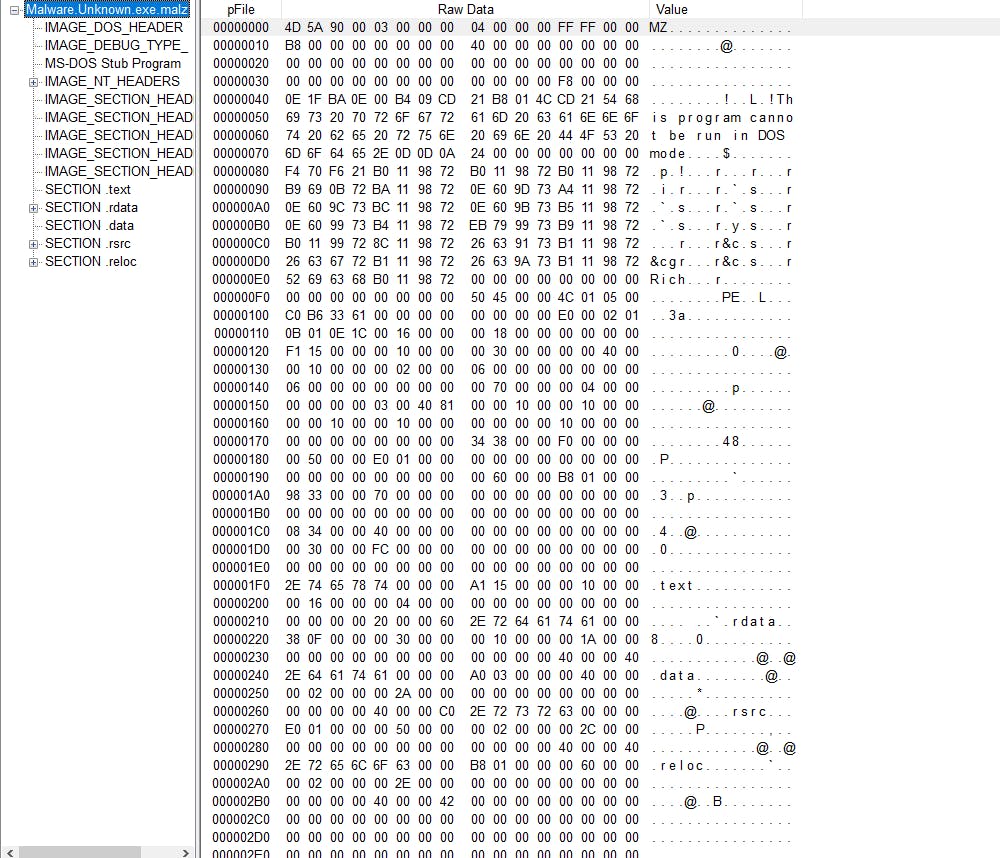
Taking a closer look at the magic bytes, we learn that this artifact is a window executable.
To understand what we're looking at, let's take a step back and read about the anatomy of PE. From there, let's head over to find out more about this file.
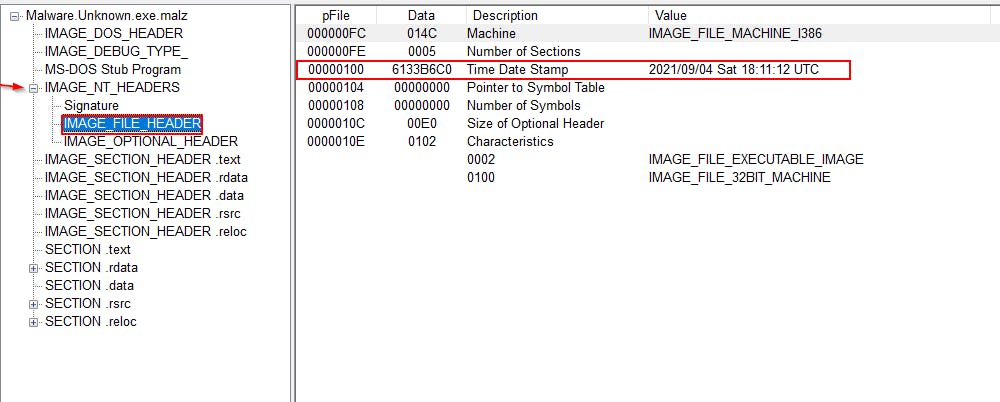
Under the IMAGE_NT_HEADERS section, we find an interesting section called IMAGE_FILE_HEADER where we find some pretty important bytes; The Time Date Stamp which tells us about when the piece of malware was compiled. Mind you, some advanced threat actors who want to stay hidden and keep us in a loop can change this information.
Also, it can tell us which compiler was used. For example, the Delphi compiler has a Date Time Stamp of 1992.
From here, we move to the IMAGE_SECTION_HEADER.text where we get to learn about the size of the executable
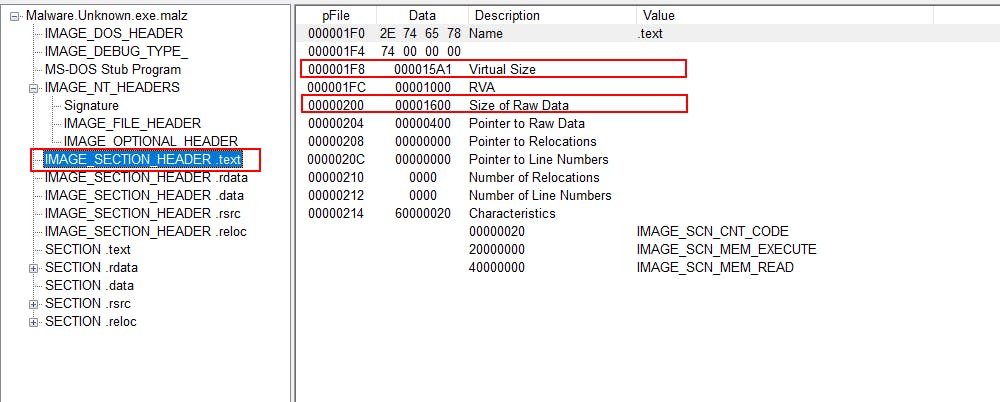
By comparing the size of the Raw Data and the Virtual Size which is roughly similar we can ascertain that the size of the raw data is the same as the virtual size. We can think of the virtual size as the amount of data on disk when the binary is run. If the size of the virtual size is much higher than the raw data then we know there's more to the binary than what is initially available, meaning the binary is packed.
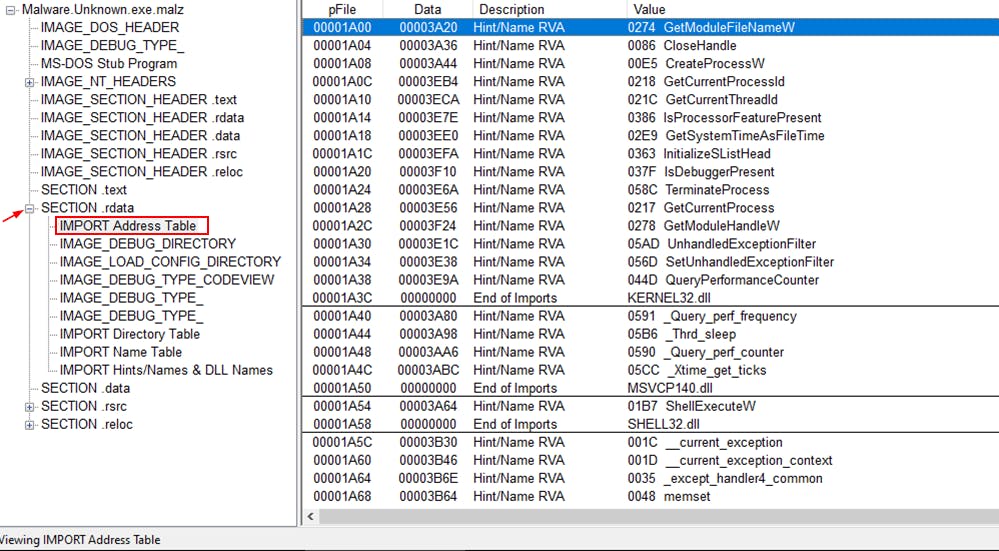
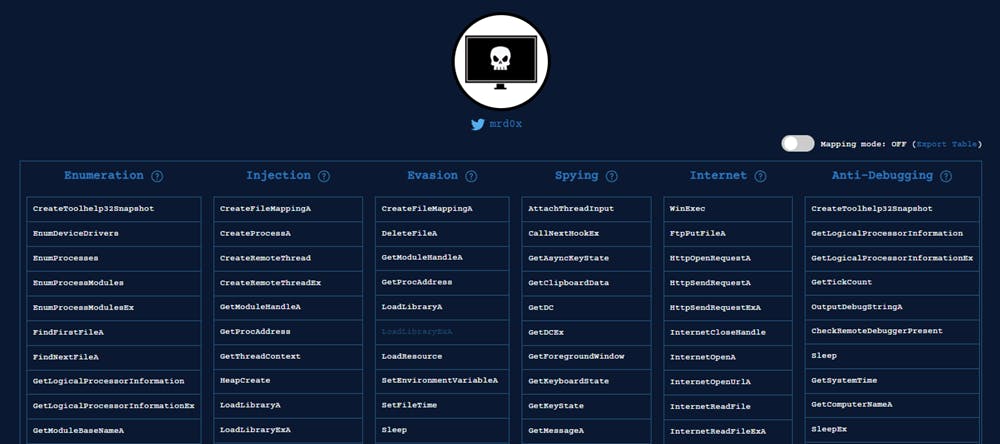
Looking at the results from the IMPORT Address Table we see a handful of Windows APIs. Windows API develops applications that run successfully on all versions of Windows while taking advantage of the features and capabilities unique to each version. This in itself is not bad but threat actors use this for their purposes. Malapi by mr.d0x maps Windows APIs to common techniques used by malware.
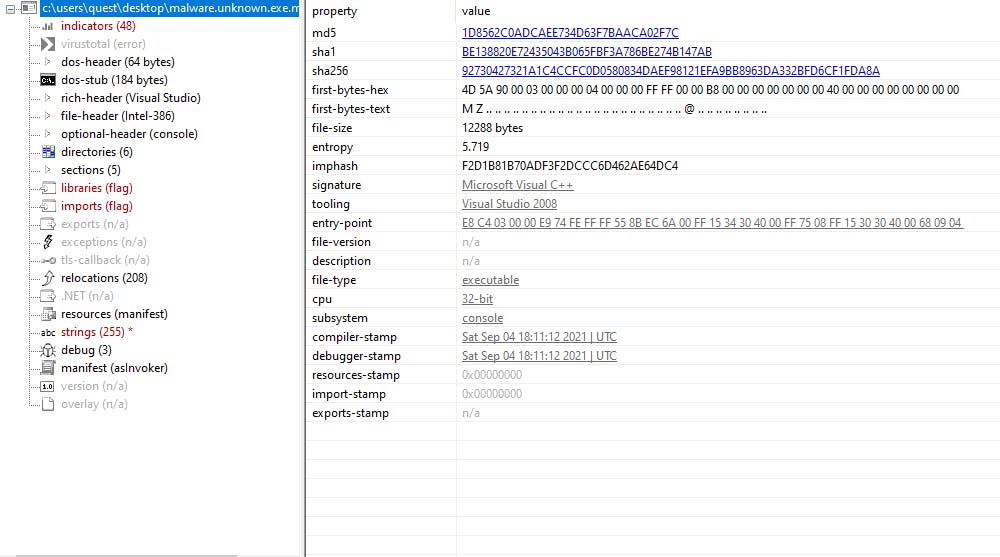
Another way of speeding up the basic static analysis process is by using Pestudio. Here we get to see tons of data to go through before moving on to dynamically analyzing this artifact.
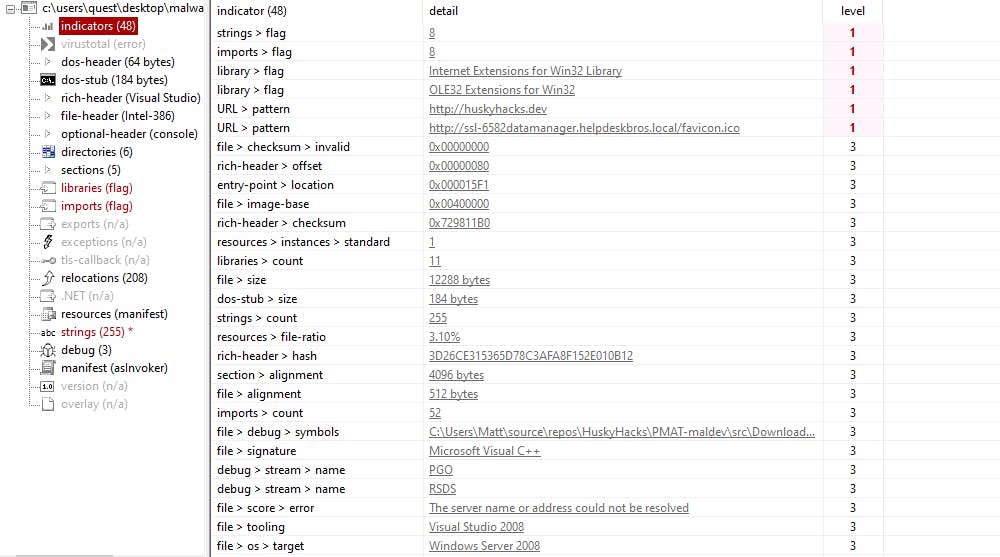
By performing basic static analysis, we get to find the indicators of compromise (IOC) and make educative guesses on what the binary is doing.
From here we move on to basic dynamic analysis which will be covered in the next part of this series. Stay tuned!

