Introduction To Android Architecture, How They Work And Security.
An overview on how android applications work and how they are secured.
This week, I would like to dive into the android architecture and how it works. As you know, the mobile devices we carry are one of the most secure devices you have and also contain a lot of personal information about you.
Hey everyone, it’s Alex and we’re back again with another post in MAPS. Without further ado, let’s dive straight in.
Introduction To Android Architecture And Security
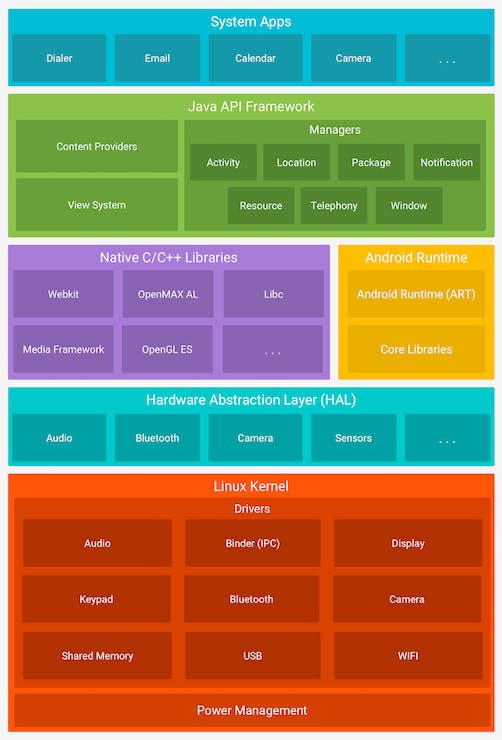
Android is based on the Linux operating system, meaning your android phone can take commands just like any Linux device. For example, ls, cd, rm, etc.
If you're unfamiliar with these terms, I would recommend you look at Tryhackme's Linux Basics or check out Bandit on overthewire.
This also means permissions to folders and applications are dependent on the Linux Operating System file permission model.
Because of this, every application is run in a virtual machine known as the android runtime. This brings me to...
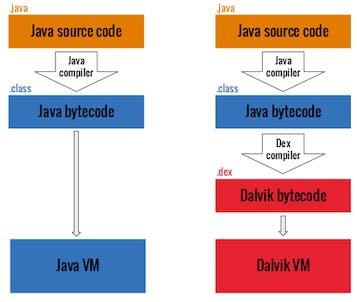
The Difference Between Dalvik and The Android Runtime
Dalvik is not utilized in modern Android OS and has been replaced by the ART. Dalvik was the original runtime VM, and is still referenced to by the name Dalvik bytecode.
Android Runtime (ART) is the modern translation layer from the application's bytecode to device instructions. Meaning every app runs in its own sandboxed virtual machine by creating a new user unique for that application creating isolation in the file system.
To get access to other folders and files we need to have root privileges and know the different profiles and users that can be created on an android system.
More information can be found on the official android website and the mobile pentest Gitbook
Since we would be analyzing the source code at some point to find vulnerabilities it's worth knowing that older apps were created in Java while newer ones are often built in kotlin after Google announced it to be the preferred coding standard in 2019.
When it comes to…
Android Application Security
Every android application can be reverse-engineered, rebuilt, re-signed and re-run which means an attacker can modify an application functionality by using a tool like JADX-GUI or Apktool which allows us to view the source code.
How does security work on android?
When developers create an app in java or kotlin, they then compile the app into DEX bytecode and for an attacker or security researcher getting readable code is crucial. To archive this, the Dex bytecode is converted into SMALI which is then converted into the decompiled Java for analysis.
Another way of securing android applications and ensuring their integrity is through...
Application Signing
This time we would be relying on public-key cryptography. When a developer has an application ready to be uploaded to Google Play Store, the app is signed with tools like keytool ,jarsigner, and zipalign. In addition, Google implemented Google Play signing which adds unique signatures to the apps before a user downloads an app.
Today there are three methods of verifying signatures which includes APK Signature scheme v1, v2 and v3.
Why is this relevant?
At some point during the analysis, we would have to get root access to the file system to get full access to the application's resources.
That’s it for this week and as always, if you’re enjoying this series consider following me here and don’t forget to like, comment and share.